Upgrading qmail
April 25, 2025 by Roberto Puzzanghera 557 comments
- Latest version 2025.04.30 (github)
- Changelog
- Readme
For my convenience I moved the qmail sources to my github space. Nonetheless, all information about qmail and related programs will continue to be posted in this web space, and this pages remain the place to eventually seek support. From now on, instead of releasing a combined patch for qmail, I'll release a package which is the result of the ancient netqmail-1.06 plus my modifications. The original patches that I accomodated in my qmail package are listed below.
Changelog
- Apr 30, 2025
qmailctlqmHandle,queue_repairand all scripts installed in QMAIL/bin and not in /usr/local/bin byconfig-all.sh - Apr 25, 2025
- added a configuration script config-all, which configure and installs the control files (as per the original config-fast script), aliases, SRS (uses control/me as the srs_domain), log dirs in /var/log/qmail, tcprules (basic, just to make initial tests), supervise scripts,qmailctlscript, DKIM control/filterargs and control/domainkeys dir, SURBL,smtpplugins,helodnscheckspp plugin,svtools,qmHandle,queue-repair, SSL key file (optional).
Consider this feature as "testing" - Feb 11, 2025
- Several adjustments to get freeBSD and netBSD compatibility. More info in the commit history. Hints/comments are welcome.
- freeBSD users have to leave the very 1st line of the file "conf-lib" blank, as libresolv.so is not needed on freeBSD.
- Dropped files install-big.c, idedit.c and BIN.* files.
- Dropped files byte_diff.c, str_cpy.c, str_diff.c, str_diffn.c and str_len.c, which break compilation on clang and can be replaced by the functions shipped by the compiler (tx notqmail).
- Old documentation moved to the "doc" dir. install.c and hier.c modified accordingly
- conf-cc and conf-ld now have -L/usr/local/lib and -I/usr/local/include to look for srs2 library
- conf-cc and conf-ld now have -L/usr/pkg/lib and -I/usr/pkg/include to satisfy netBSD
- vpopmail-dir.sh: minor correction to vpopmail dir existence check
- srs.c: #include <srs2.h> now without path - Dec 01, 2024 (More info here and in the github release notes)
- Added support for EAI (RFC 5336 SMTP Email Address Internationalization) (#13). Thanks to https://github.com/arnt/qmail-smtputf8/tree/smtputf8-tls. libidn2 package (libidn2-dev on debian) is a new dependence.
- chkuser is now smtputf8 compliant. It accepts utf8 characters in sender and recipient addresses provided that the remote server advertises the SMTPUTF8 verb in MAIL FROM, otherwise it allows only ASCII characters plus additional chars from the CHKUSER_ALLOWED_CHARS set.
* dropped variables CHKUSER_ALLOW_SENDER_CHAR_xx CHKUSER_ALLOW_RCPT_CHAR_xx (replaced by CHKUSER_ALLOWED_CHARS)
* dropped variables CHKUSER_ALLOW_SENDER_SRS and CHKUSER_ALLOW_RCPT_SRS, as we are always accepting '+' and '#' characters
* added variables CHKUSER_INVALID_UTF8_CHARS and CHKUSER_ALLOWED_CHARS - Oct 26, 2024
- qmail-remote.c patched to dinamically touch control/notlshosts/<fqdn> if control/notlshosts_auto contains any number greater than 0 in order to skip the TLS connection for remote servers with an obsolete TLS version. (tx Alexandre Fonceca) (commit)
- defined CHKUSER_DISABLE_VARIABLE "RELAYCLIENT" in chkuser_settings.h
- enabled CHKUSER_SENDER_NOCHECK_VARIABLE "RELAYCLIENT" in chkuser_settings.h
- fixed several compilation breaks/warnings on later gcc compilers (tx Pablo Murillo)
- invalid auth fix in qmail-smtpd.c's smtp_auth function (tx Alexandre Fonceca for the advice) (commit)
- qmail path determined dinamically in conf-policy - Jan 11, 2024
- DKIM: dk-filter dropped
WARNING: IF YOU ARE UPGRADINGqmailAND YOU ARE USING A VERSION BEFORE 2024.01.11, YOU HAVE TO RECONFIGURE DKIM AND MODIFY YOURrcFILE ACCORDINGLY.
Configuring qmail
April 18, 2025 by Roberto Puzzanghera 107 comments
- More info on Life with qmail
- README.vdelivermail
qmail v2025.04.18 and later include a new config-all script to automate the qmail core configuration. Several scripts are now embedded in qmail and automatically installed if one simply run './config-all mx.domain.tld' after the compilation. This is what will be installed and configured by the quick installation:
- main control files as per original
config-fastscript, - aliases,
- RBL
- SPF
- SRS (uses control/me as the srs_domain),
- log dirs in /var/log/qmail,
- cronjobs
- logrotate
- PATH and MANPATH in /etc/profile.d/qmail.sh
- tcprules (basic, just to make initial tests),
- supervise scripts,
qmailctlscript,- DKIM control/filterargs and control/domainkeys dir,
- SURBL,
- overlimit feature,
- moreipme,
- smtpplugins,
helodnscheckspp plugin,svtools,qmHandle,queue-repair,- SSL key file (optional)
From now on, running ./config-all mx.mydomain.tld after the compilation will get the qmail installation ready for testing. You'll only have to add your virtual domains and the other features not listed above.
Those who prefer to manually configure everything can stick with the original config-fast script, which now copies my supervise scripts to the qmail/doc dir.
In the following, the "Manual configuration" section is of course a suggested reading in order to have a view of how everything works, especially for newbies.
Consider this feature as testing for the time being. Feedbacks are appreciated.
Changelog
- Apr 15, 2025
- added script config-all.sh - Jul 31, 2024
- multilog uses "d" flag as default to gain compatibility with the readable datetime format of multilog in daemontools-0.78. Change it with the "t" flag if you prefer to have timestamps.
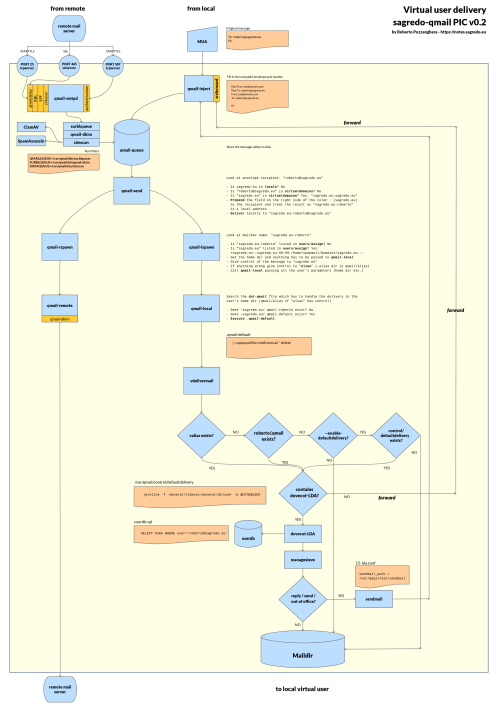
Qmail virtual user delivery picture
April 3, 2025 by Roberto Puzzanghera 0 comments
The architecture of my qmail configuration has been customized a lot over the years, expecially as far as the delivery for a virtual user is concerned when one enables my "defaultdelivery" feature for vpopmail (--enable-defaultdelivery) that I modified recently, so I have built a qmail picture with the intent of clarify how things works together.
It's obviously inspired by the PICs by djb and by the André Oppermann's "Big qmail picture".
Installing and configuring VPopMail
March 29, 2025 by Roberto Puzzanghera 145 comments
VPopMailversion: 5.6.8- github: sagredo-dev/vpopmail
- Download
- Changelog
- README.vdelivermail
- Inter7's original page
Vpopmail provides an easy way to manage virtual email domains and non /etc/passwd email accounts on your mail servers.
Changelog
- Mar 29, 2025 (v5.6.8)
defaultdelivery feature (--enable-defaultdelivery) changes (more info here, commit):vdelivermailis installed by default in .qmail-default of newly created domains with option 'delete' as in the previous version.- if no user's valiases and no .qmail are found, then the message is sent to the control/defaultdelivery file, so that
dovecot-lda(or whatelse) can execute the sieve rules and finally store the message into inbox. - if vdelivermail is found in control/defaultdelivery, then it is ignored to avoid loops. The delivery is done by
vdelivermail - v. 5.6.8 is backward compatible. The users having .qmail from previous versions of the defauldelivery feature are not affected by this change.
- Mar 23, 2025 (v. 5.6.7)
- bug fix in vpopmaild.c: Crypted[64] enlarged to Crypted[128] to make room for SHA-512 passwords. This restores the usability of the RoundCube's 'password' plugin (commit)
- fixed quota calculation in sql procedures for dovecot (tx Hakan Cakiroglu) (commit)
- minor changes to the usage function of vmakedotqmail.c (commit) - Feb 9, 2025 (v. 5.6.5)
- added pwd strength check also for vadduser.c
- removed-std=c99 -D_XOPEN_SOURCE=500arguments fromCFLAGSin configure.ac to makeclanghappy
- several changes to compile onFreeBSD clangv. 18.1.6 - Dec 20, 2024 (v 5.6.4)
- Password strength enforcement (PR #5, grabbed from Matt Brookings' 5.5.0-dev version)
- Dropped min pwd length feature.
- vmysql.h: tables' layout changed in order to have VARCHAR instead of CHAR. Fields containing ip addresses enlarged to VARCHAR(39), to create room for ipv6. Unix timestamps definition changed from BIGINT(20) to INT(11). (commit 44bad58) Have a look to the upgrade notes below. - Oct 14, 2024 (v. 5.6.2)
- fixed a configure break where a trivial C test program exits on error with gcc-14.1 due to missing headers
- vusaged/domain.c: fixed -Wimplicit-function-declaration compilation warning
- vmysql.h: dropped the multicolumn PRIMARY KEY in valias table to allow multiple forwards for a given alias.
In case one already has the valias table defined, this is the sql query for the upgrade:
ALTER TABLE `vpopmail`.`valias` DROP PRIMARY KEY, ADD INDEX (`alias`, `domain`, `valias_type`) USING BTREE;
ALTER TABLE `vpopmail`.`valias` ADD `id` INT NOT NULL AUTO_INCREMENT FIRST, ADD PRIMARY KEY (`id`);
Installing Dovecot and sieve on a VpopMail + qmail server
March 29, 2025 by Roberto Puzzanghera 109 comments
Changelog
- Mar 29, 2025
- dovecot updated to v. 2.4.1-4
-dovecot_config_versionanddovecot_storage_versionflags changed to '2.4.1' in dovecot.conf - Mar 15, 2025 (config version 2.4.0.1 diff)
- Added quota warnings feature. Improved quota configuration in 90-quota.conf (more info here)
- Configured auth-master.conf.ext and auth-deny.conf.ext. To be included in local.conf - Mar 9, 2025
- fixed quota calculation in sql queries (tx Hakan Cakiroglu) (commit) - Feb 22, 2025 (version 2025.02.25b)
- Bug fix in 90-sieve.conf: global script to move spam into Junk now working
- Bug fix in move-spam.sieve: it was erroneously matching "YES" in the header if "BAYES" was present (Feb 15, 2025 config version not affected, no need to recompile the sieve script) - Feb 15, 2025
- added support forvpopmailconfigured with--disable-many-domains - Feb 8, 2025
- dovecot_postlogin.sh: query changed in order to add new records as well (tx Bai Borko)
- bug fix: pop3 service was executing imap instead of pop3 (tx Gabriel Torres) - Jan 29, 2025
- dovecot upgraded to v. 2.4.0. Old configuration files are not valid anymore and you have to install dovecot from scratch. - Nov 15, 2024
- added a postlogin script to update the vpopmail.lastauth SQL table on login (see 10-master.conf, thanks kengheng) - Dec 29, 2023
default_pass_scheme = SHA512-CRYPT (was MD5-CRYPT) in dovecot-sql.conf.ext, as vpopmail-5.6.x has now SHA512-CRYPT password by default
Setting up your firewall with Fail2Ban
March 14, 2025 by Roberto Puzzanghera 23 comments
- Version: 1.1.0
- More info here
- Howto (Wiki)
- Manual
Fail2ban scans log files (e.g. /var/log/apache/error_log) and bans IPs that show the malicious signs -- too many password failures, seeking for exploits, etc. Generally Fail2Ban is then used to update firewall rules to reject the IP addresses for a specified amount of time, although any arbitrary other action (e.g. sending an email) could also be configured. Out of the box Fail2Ban comes with filters for various services (apache, courier, ssh, etc).
I will show shortly how to install and configure fail2ban to ban malicious IPs, especially those related to the qmail-dnsrbl patch. This will avoid to be banned ourselves by spamhaus, which is free up to 100.000 queries per day.
fail2ban requires that you have a firewall as nftables or iptables active.
Changelog
- Mar 14, 2025
- dovecot filter updated for dovecot 2.4 - May 1, 2024
- Fail2Ban upgraded to v. 1.1.0 (changelog)
* This version drops the python2 support
* newfail2ban-client statscommand returns statistic in form of table (jail, backend, found and banned counts) - Jul 15, 2023
- the installation and the configuration has been revised in order to work onDebian,wherepython2is missing (tx Gabriel Torres) - Nov 20, 2022
- switched all actions tonftables, as it has now replacediptablesandfail2banhas support for it. Just replace "iptables" with "nftables" in your jails. - Nov 18, 2022
- Fail2Ban upgraded to v. 1.0.2
- jails now have a different action's declaration (iptables[type=multiport] instead of iptables-multiport[])
- added a short note on how to configure the server with a network bridge
autorespond
March 12, 2025 by Roberto Puzzanghera 31 comments
- github repo
- Latest version: 2.0.9
- README
- Changelog
- Original author: Inter7
autorespond is used for vacation messages. It's required by qmailadmin.
Changelog
- Mar 12, 2025
- bug fix in memory allocation which caused a segfault when To: address has be used (tx Stephan for the hint)
Roundcube webmail
March 9, 2025 by Roberto Puzzanghera 16 comments
- Info: https://roundcube.net
- Version: 1.6.10
Roundcube is a full featured webmail with a nice interface.
Changelog
- Mar 9, 2025
added$config['quota_zero_as_unlimited'] = true;to show quota unlimited instead of unknown for accounts with unlimited quota - Feb 9, 2025
RC update to v. 1.6.10 - Gen 21, 2024
RC upgraded to v. 1.6.6
-new $config['imap_host'] variable
-all my SMTP config options were stripped from my configuration file and I had to restore them - Jan 3, 2021
disabled the SMTP authentication when sending messages via RC. SMTP port changed to 25.
Read the release note at https://github.com/roundcube/roundcubemail/blob/master/CHANGELOG.md for more info.